Generate Initial Synapse Config And Signing Key Failed Matrix-synapse
Unknown service 'matrix-synapse' + sudo yunohost service remove matrix-synapse W: GPG error: http: // httpredir.debian.org jessie Release: The following signatures couldn 't be verified because the public key is not available: NOPUBKEY 8B48AD NOPUBKEY 7638D0442B90D010 NOPUBKEY CBF8D6FD518E17E1. Stack Exchange network consists of 175 Q&A communities including Stack Overflow, the largest, most trusted online community for developers to learn, share their knowledge, and build their careers. Mar 05, 2018 @Half-Shot This is all my file homeserver.yaml: # vim:ft=yaml # PEM encoded X509 certificate for TLS. # You can replace the self-signed certificate that synapse # autogenerates on launch with your own SSL certificate + key pair # if you like.
- synapse wurde nicht ordnungsgemäß entfernt
- + sudo yunohost service remove matrix-synapse
- W: GPG error: http://httpredir.debian.org jessie-backports InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 8B48AD6246925553 NO_PUBKEY 7638D0442B90D010
- + DEBIAN_FRONTEND=noninteractive
- + ynh_package_update
- + sudo rm -rf /etc/apt/sources.list.d/matrix.list
- Close port 5349
- + grep -q '- 5349$'
- + closeport
- + sudo yunohost firewall disallow TCP 8448
- + echo 'Close port 8448'
- + sudo yunohost firewall list
- + port=8448
- + REMOVE_LOGROTATE_CONF
- + sudo rm /etc/nginx/conf.d/MY.DOMAIN.XXX.COM.d/synapse.conf
- + echo 'Delete nginx config'
- + '[' -e /etc/nginx/conf.d/MY.DOMAIN.XXX.COM.d/synapse.conf ']'
- + true
- E: Unable to locate package python-matrix-synapse-ldap3
- + sudo apt-get -y -qq autoremove matrix-synapse python-matrix-synapse-ldap3 coturn
- + ynh_apt autoremove matrix-synapse python-matrix-synapse-ldap3 coturn
- + ynh_package_autoremove matrix-synapse python-matrix-synapse-ldap3 coturn
- Failed to stop coturn.service: Unit coturn.service not loaded.
- + true
- Failed to stop matrix-synapse.service: Unit matrix-synapse.service not loaded.
- + turnserver_tls_port=5349
- ++ sudo yunohost app setting synapse turnserver_tls_port --output-as plain --quiet
- ++ ynh_app_setting_get synapse turnserver_tls_port
- ++ sudo yunohost app setting synapse synapse_tls_port --output-as plain --quiet
- + domain=MY.DOMAIN.XXX.COM
- ++ sudo yunohost app setting synapse domain --output-as plain --quiet
- + ARCHITECTURE=arm
- ++ grep arm
- + '[' -n '' ']'
- ++ uname -m
- ++ uname -m
- + test jessie jessie
- + debian_version=jessie
- + GET_DEBIAN_VERSION
- + CHECK_VAR synapse 'app name not set'
- ++ . /usr/share/yunohost/helpers.d/utils
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/user ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/string ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/setting ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/print ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/package ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ . /usr/share/yunohost/helpers.d/mysql
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/ip ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ . /usr/share/yunohost/helpers.d/filesystem
- ++ '[' -r /usr/share/yunohost/helpers.d/filesystem ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- +++ run-parts --list /usr/share/yunohost/helpers.d
- + set -eu
- ++ python_ujson_version=1.35-1
- ++ md5sum_python_ujson=5b65f8cb6bedef7971fdc557e09effbe
- ++ md5sum_python_nacl=34c44f8f5100170bae3b4329ffb43087
- ++ debian_repos=http://httpredir.debian.org/debian/
- Skript '/var/cache/yunohost/from_file/synapse_ynh-master/scripts/remove' wird ausgeührt..
- + sudo apt-get -y -qq -o Dpkg::Options::=--force-confdef -o Dpkg::Options::=--force-confold install coturn
- + ynh_apt -o Dpkg::Options::=--force-confdef -o Dpkg::Options::=--force-confold install coturn
- + sudo debconf-set-selections
- + echo 'matrix-synapse matrix-synapse/report-stats selectfalse'
- + echo 'matrix-synapse matrix-synapse/server-name select MY.DOMAIN.XXX.COM'
- + sudo apt-key add /tmp/matrix-repo-key.asc
- + wget -q -O /tmp/matrix-repo-key.asc https://matrix.org/packages/debian/repo-key.asc
- + sudo sed -i s@__PORT__@8008@g /etc/nginx/conf.d/MY.DOMAIN.XXX.COM.d/synapse.conf
- + sudo sed -i s@__PATH__@/_matrix@g /etc/nginx/conf.d/MY.DOMAIN.XXX.COM.d/synapse.conf
- + sudo cp ./conf/nginx.conf /etc/nginx/conf.d/MY.DOMAIN.XXX.COM.d/synapse.conf
- + sudo yunohost app setting synapse turnserver_pwd -v 1EZeOrvefWLEMotFLEOVpdmcVUvmIa --quiet
- + ynh_app_setting_set synapse turnserver_pwd 1EZeOrvefWLEMotFLEOVpdmcVUvmIa
- + sudo yunohost app setting synapse turnserver_tls_port -v 5349 --quiet
- + ynh_app_setting_set synapse turnserver_tls_port 5349
- + sudo yunohost app setting synapse synapse_tls_port -v 8448 --quiet
- + ynh_app_setting_set synapse synapse_tls_port 8448
- + sudo yunohost app setting synapse synapse_port -v 8008 --quiet
- + sudo yunohost app setting synapse is_public -v 1 --quiet
- + sudo yunohost app setting synapse path -v /_matrix --quiet
- + sudo yunohost app setting synapse domain -v MY.DOMAIN.XXX.COM --quiet
- + ynh_app_setting_set synapse domain MY.DOMAIN.XXX.COM
- ++ sed -n 's/(.{30}).*/1/p'
- ++ dd if=/dev/urandom bs=1 count=200
- .......................+........+................+............................++*++*
- Generating DH parameters, 2048 bit long safe prime, generator 2
- + sudo openssl dhparam -out /etc/yunohost/certs/MY.DOMAIN.XXX.COM/dh.pem 2048
- + test '!' -e /etc/yunohost/certs/MY.DOMAIN.XXX.COM/dh.pem
- + sudo yunohost firewall allow --no-upnp Both 5349
- + turnserver_tls_port=5349
- ++ netcat -z 127.0.0.1 5349
- ++ port=5349
- + synapse_port=8008
- ++ netcat -z 127.0.0.1 8008
- ++ port=8008
- + synapse_tls_port=8448
- ++ netcat -z 127.0.0.1 8448
- ++ port=8448
- + '[' -e /var/www/synapse ']'
- + CHECK_FINALPATH
- + sudo yunohost app checkurl MY.DOMAIN.XXX.COM/_matrix -a synapse
- + '[' x / ']'
- + CHECK_PATH
- + path=/_matrix
- + ARCHITECTURE=arm
- ++ grep arm
- + '[' -n '' ']'
- ++ uname -m
- ++ grep 64
- + test jessie jessie
- + debian_version=jessie
- + GET_DEBIAN_VERSION
- + CHECK_VAR synapse 'app name not set'
- ++ . /usr/share/yunohost/helpers.d/utils
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/user ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/string ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/setting ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/print ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/package ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ . /usr/share/yunohost/helpers.d/mysql
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ '[' -r /usr/share/yunohost/helpers.d/ip ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- ++ . /usr/share/yunohost/helpers.d/filesystem
- ++ '[' -r /usr/share/yunohost/helpers.d/filesystem ']'
- ++ for helper in '$(run-parts--list/usr/share/yunohost/helpers.d 2>/dev/null)'
- +++ run-parts --list /usr/share/yunohost/helpers.d
- + set -eu
- ++ python_ujson_version=1.35-1
- ++ md5sum_python_ujson=5b65f8cb6bedef7971fdc557e09effbe
- ++ md5sum_python_nacl=34c44f8f5100170bae3b4329ffb43087
- ++ debian_repos=http://httpredir.debian.org/debian/
- Skript '/var/cache/yunohost/from_file/synapse_ynh-master/scripts/install' wird ausgeührt..
- Erledigt.
- Wird heruntergeladen..
Related
Introduction
Matrix is an open standard for decentralized communication. It’s a collection of servers and services used for online messaging which speak a standardized API that synchronizes in real time.
Matrix uses homeservers to store your account information and chat history. They work in a similar way to how an email client connects to email servers through IMAP/SMTP. Like email, you can either use a Matrix homeserver hosted by somebody else or host your own and be in control of your own information and communications.
By following this guide you will install Synapse, the reference homeserver implementation of Matrix. When you’re finished, you will be able to connect to your homeserver via any Matrix client and communicate with others users across other Matrix federated homeservers.
Prerequisites
Before you begin this guide you’ll need the following:
One Ubuntu 16.04 server set up by following this initial server setup guide, including a sudo non-root user and a firewall.
Nginx installed on your server (allowing for HTTPS traffic); you can do this by following this Nginx on Ubuntu 16.04 tutorial.
A registered domain name set up with the appropriate DNS records by following this hostname tutorial. Which DNS records you need depend on how you’re using your domain.
- If you’re using your domain exclusively for Synapse, or if you will be using the same server to host your website and Synapse, you only need an A record with the hostname
@. - If you will be installing Synapse on a separate server, you will need an A record with the hostname set to the subdomain you want to use, like
matrix.example.com, and a SRV record with the hostname_matrix._tcppointing to the same subdomain on port8448, with the default priority and weights of 10 and 100 respectively. This will tell Matrix clients and homeservers where to find your Synapse installation.
- If you’re using your domain exclusively for Synapse, or if you will be using the same server to host your website and Synapse, you only need an A record with the hostname
Generate Initial Synapse Config And Signing Key Failed Matrix-synapse Version
Step 1 — Installing Matrix Synapse
Log in to your server as your non-root user to begin.
Before you start installing anything, make sure your local package index is up to date.
Next, add the official Matrix repository to APT.
To make sure your server remains secure, you should add the repository key. This will check to make sure any installations and updates have been signed by the developers and stop any unauthorized packages from being installed on your server.
You’ll see the following output:
After adding the repository, update the local package index so it will include the new repository.
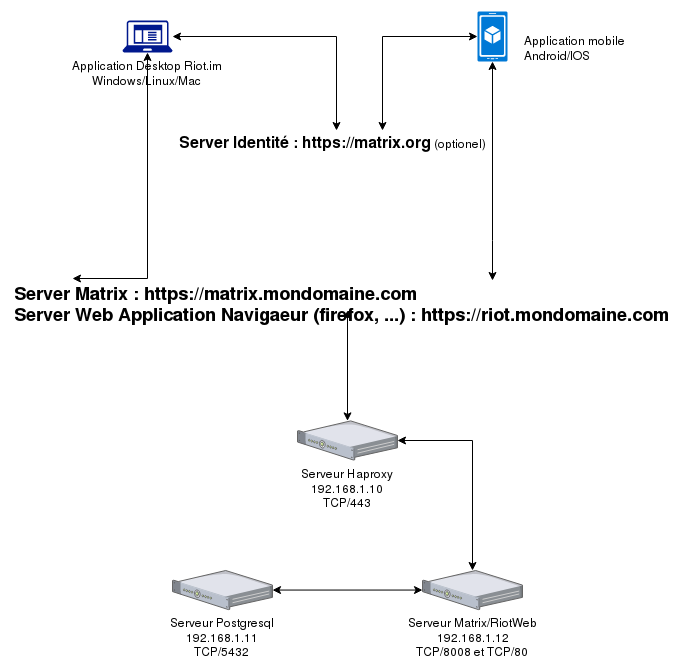
With the repository added, installing Synapse is as simple as running a single APT command.
During the installation, you will be prompted to enter a server name, which should be your domain name. You will also be asked to choose whether or not you wish to send anonymized statistics about your homeserver back to Matrix. Then, Synapse will install.
Once complete, use systemctl to automatically start Synapse whenever your server starts up.
That command only starts Synapse when the whole server starts. Your server is already running, so use systemctl manually to start Synapse now.
Synapse is now installed and running on your server, but you’ll need to create a user before you can start using it.
Step 2 — Creating a User for Synapse
Before you can start using Synapse, you will need to add a user account. Before you can add a new user, you need to set up a shared secret. A shared secret is a string that can be used by anybody who knows it to register, even if registration is disabled.
Use the following command to generate a 32-character string.
Copy the string you create, then open the Synapse configuration file with nano or your favorite text editor.
In the registration section, look for the registration_shared_secret key. Update its value to the random string you copied, inserting it between quotation marks (' '). Remember to activate the key by uncommenting the line (i.e. deleting the # at the beginning of the line).
If you want to enable public registration as well, you can update the value of enable_registration to True here.
Save and close the file.
After modifying the configuration, you need to restart Synapse so the changes can take effect.
Once restarted, use the command line to create a new user. The -c flag specifies the configuration file, and uses the local Synapse instance which is listening on port 8448.
You will be prompted to choose a username and a password. You’ll also be asked if you want to make the user an administrator or not; it’s up to you, but an administrator isn’t necessary for this tutorial.
Once your user is created, let’s make sure the webserver is able to serve Synapse requests.
Generate Initial Synapse Config And Signing Key Failed Matrix-synapse Download
Step 3 — Configuring Nginx and SSL
Matrix clients make requests to https://example.com/_matrix/ to connect to Synapse. You’ll need to configure Nginx to listen for these requests and pass them on to Synapse, which is listening locally on port 8008. You’ll also secure your setup by using SSL backed by Let’s Encrypt.
Generate Initial Synapse Config And Signing Key Failed Matrix-synapse Password
To do this, you’ll create a custom Nginx configuration file for your website. Create this new configuration file.
The location /_matrix block below specifies how Nginx should handle requests from Matrix clients. In addition to the request handling, the /.well-known block makes the directory of the same name available to Let’s Encrypt.
Copy and paste the following into the file.
This Nginx server blocks tutorial has more information about how files like these work. When you have configured the server, you can save and close the file.
To enable this configuration, create a symlink for this file in the /etc/nginx/sites-enabled directory.
Test your configuration file for syntax errors by running the command.
Correct the syntax based on the error output, if any. When no errors are reported, use systemctl reload Nginx so the changes take effect.
To finish securing Nginx with a Let’s Encrypt certificate, follow this Let’s Encrypt for Nginx on Ubuntu 16.04 tutorial. Remember to use /etc/nginx/sites-available/example.com instead of the default configuration file. You’ve already added the ~/.well-known block mentioned in Step 2 of that tutorial.
Once Let’s Encrypt is set up, you can move on to configuring the firewall to allow the necessary traffic for Synapse to communicate with other homeservers.
Step 4 — Allowing Synapse through the Firewall
Client traffic connects to Synapse via the HTTPS port 443, (which is already open in your firewall from the Nginx guide). However, traffic from other servers connects directly to Synapse on port 8448 without going through the Nginx proxy, so you need to allow this traffic through the firewall as well.
Check the status of UFW.
It should look like this:
This means that all the necessary traffic is allowed through your firewall. The last step you should take is improving Synapse’s security by updating its SSL certificates.
Step 5 — Securing Federation with SSL (Recommended)
Generate Initial Synapse Config And Signing Key Failed Matrix-synapse Update
Now that Synapse is configured and can communicate with other homeservers, you can increase its security by using the same SSL certificates you requested from Let’s Encrypt at the end of Step 3. By default Synapse uses self signed certificates which do the job, but seeing as you already requested the Let’s Encrypt certificates it’s simple to use those and improve security.
Windows 8.1 enterprise activation key generator. Copy the certificates to your Synapse directory:
In order for these certificates to be updated when they are renewed you need to add these commands to your cron tab. Open it for editing.
Generate Initial Synapse Config And Signing Key Failed Matrix-synapse Error
And add the following lines:
Then save and close the file. Next, open your Synapse configuration file with nano or your favorite text editor.
Using the same certificate you requested from Lets Encrypt in Step 3, replace the paths in the configuration file.
Generate Initial Synapse Config And Signing Key Failed Matrix-synapse Windows 10
Restart Synapse so the configuration changes take effect.
/adobe-premiere-pro-cc-2018-key-generator.html. Everything’s set up, so now you can connect to your homeserver with any Matrix client and start communicating with others. For example, you can use the client on Matrix’s website.
Enter the following for the appropriate fields:
- Your Matrix ID is in the format
@user:server_name(e.g.@sammy:example.com). Other federated servers use this to find where your homeserver is hosted. - Your Password is the secure password you set when creating this user.
- Your Home Server is the server name you chose in Step 1.
Generate Initial Synapse Config And Signing Key Failed Matrix-synapse Windows 7
If you enabled public registration in Step 2, you can also click the Create account link to create a new account or allow others to create a new account on your homeserver.
From there, you can log into rooms and start chatting. The official support room for Matrix is #matrix:matrix.org.
Conclusion
Generate Initial Synapse Config And Signing Key Failed Matrix-synapse Server
In this guide, you securely installed Matrix Synapse with Nginx, backed by SSL certificates from Let’s Encrypt. There are many Matrix clients you can use to connect to your homeserver, and you can even write your own Matrix client or get involved with the project in other ways.



